
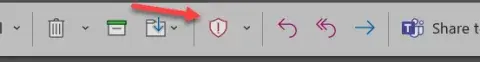
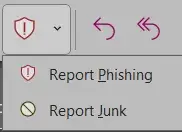
Phishing Tip 1:On Outlook client, select the Report Button, and Select one of the two options showing.
Phishing Tip 2: Block “junk” or spam email senders to reduce email clutter.
How to Block email senders:
- Open Outlook.
- Select the email you want to block.
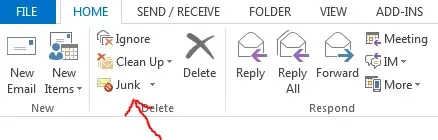
- Click “Junk” on the Outlook toolbar.
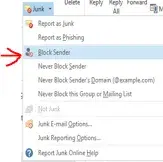
- Select “Block Sender” from the drop down menu to add the sender’s name to your personal block list. Emails from the sender will now be automatically moved to your “Junk” folder.
- Over time your “Junk Mail” folder will fill up. To empty the “Junk Mail” folder, just right click the folder and select “Empty folder.”
Phishing Tip 3: Automatically move external e.g. non-Samuel Merritt generated emails to a folder. This allows you to separate internal from external emails and reduce the likelihood of clicking on a malicious link or attachment.
How to setup an External folder:
- Open Outlook and select “Rules” on the menu bar at the top of Outlook.
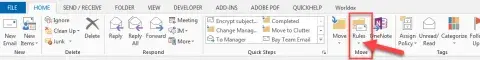
- Select the small triangle, then “Manage Rules & Alerts”
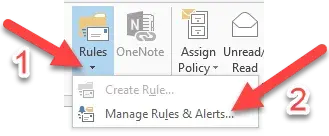
- Select “New Rule…”
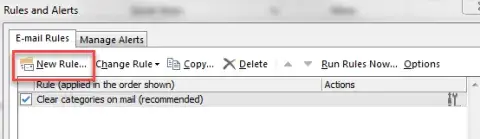
- Select “Move messages with specific words in the subject to a folder”
Click the “Next” button
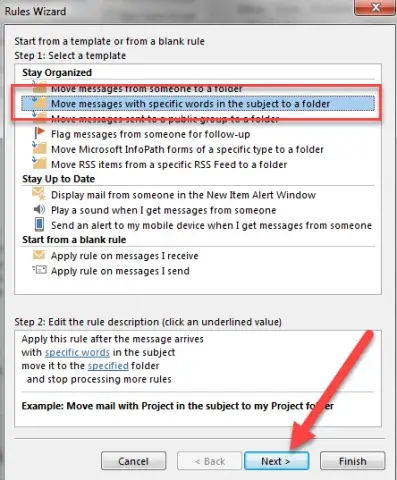
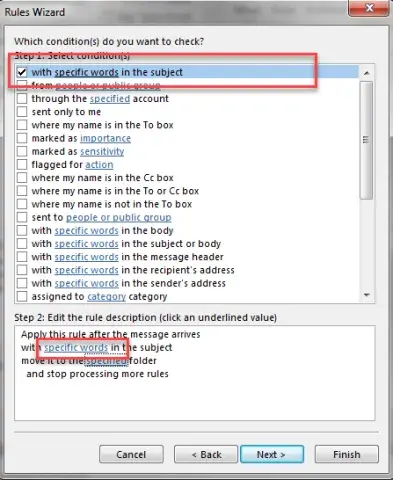
- In the “Rules Wizard” select “with specific words in the subject”.
Then click on “specific words” in Step 2 on the lower half of the box.
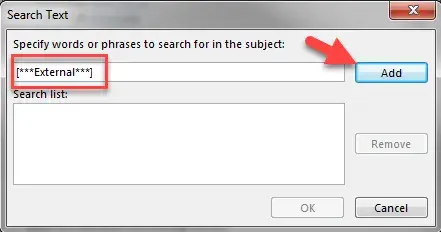
- In the “Search Text” dialog box “Specify words or phrases to search for in the subject:” type [***External***].
Then click the “Add” button.
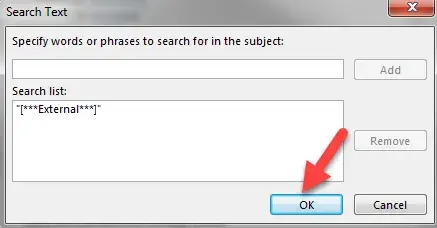
- You should see “[***External***]” in the “Search List”. Click “OK”.
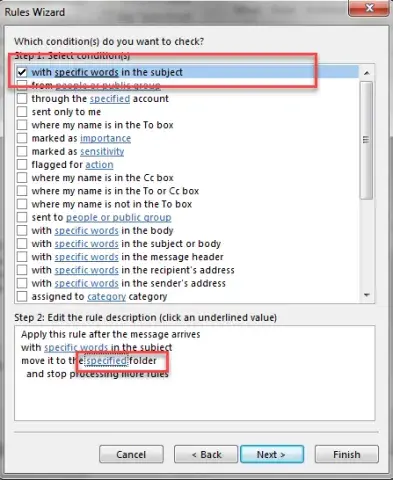
- Now click “specified” folder.
- You can chose and existing folder or a new one. To select a new folder, click the “New” button.
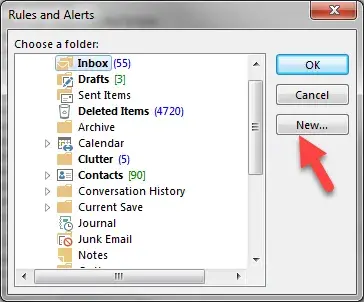
- Give the new folder a distinctive name like “***External*** Mail”
Note: using asteriks will list the folder at the top of the list of folders it is nested in.
Click “OK”.
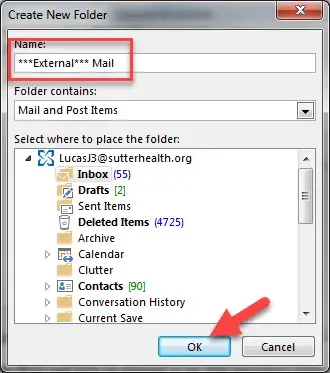
- You should now have [***External***] as the specific words in the subject, and ***External*** Mail in the move to…folder.
Click “Next”.
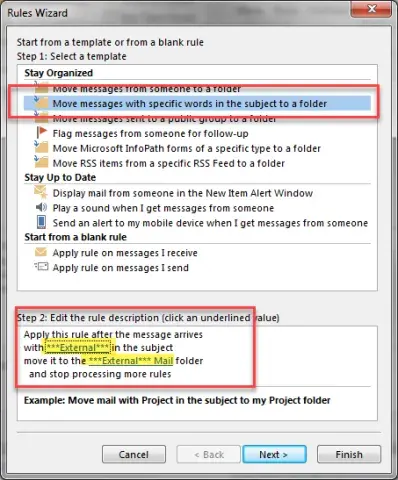
- You can click “Next”, unless you want to edit something.
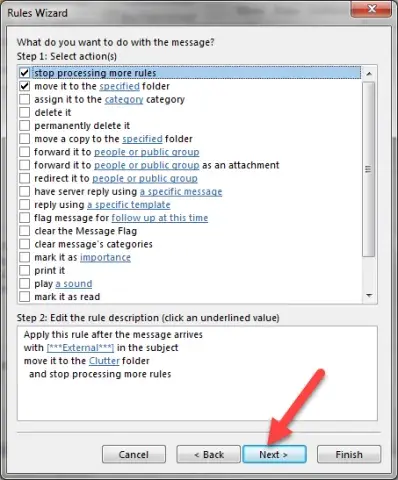
- If there are specific email addresses you KNOW are good, you can add them by selecting “except from people or public group” and adding them.
Be very cautious about using this.
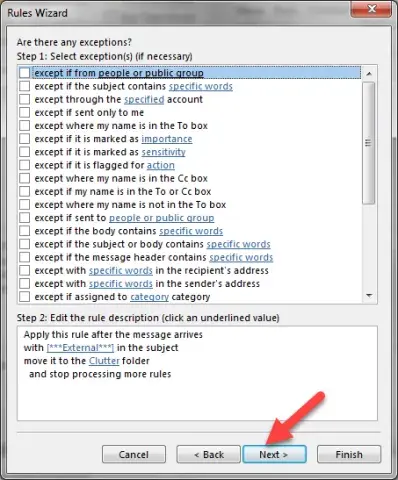
- Almost Done!
Give the Rule a name, like “***External***” that will help you understand what the rule does.
Optional: You can have the rule run now on your inbox by selecting “Run this rule now on messages already in “Inbox””.
Click “Finish”.
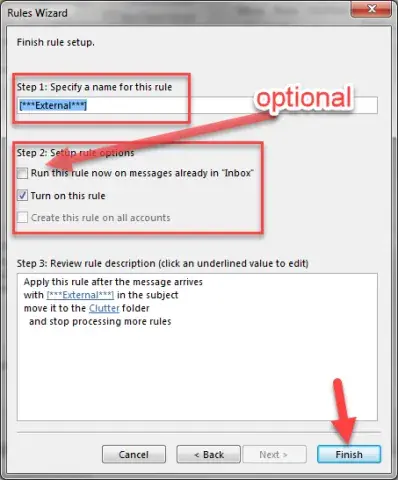
- Here is your new Rule!
Click “OK”.
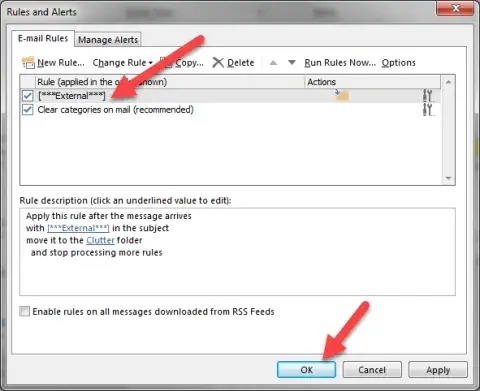
- Done!
Now that you have the ***External*** emails in a separate folder, you can review those when you have a bit more time to think carefully about them. And remember: “Be paranoid, because the bad guys really are after our patients’ information”.